WhatsApp just announced that end-to-end encrypted cloud backups will be available for Android and iOS in the near future. This ensures that your communications remain encrypted even when they are stored on a cloud provider as part of WhatsApp backups. To recap, the app has been offering end-to-end encrypted messaging to its customers since 2016, and this is simply an extension of that service.
In the following weeks, the functionality of end-to-end encrypted backups will be rolled out to both Android and iOS devices. It will be made available as an optional feature that users can enable directly within the app. In this section, we’ll look at how the end-to-end encrypted backups feature works and how to enable it when it becomes available.
How end-to-end encrypted backups work
Facebook announced in a blog post that it has created a new mechanism for storing encryption keys for Android and iOS. When the user activates the function, their backups will be encrypted with a one-of-a-kind, randomly generated encryption key. They can also choose to manually secure the key or to use a user password.
According to the business, if a user chooses to use a password, the key will be stored in a Backup Key Vault, which is constructed on a component known as a hardware security module (HSM).
When an account owner needs to access their backup, they can use their encryption key to access it, or they can use their personal password to obtain their encryption key from the Backup Key Vault and decrypt their backup.
To resist brute-force attacks, the HSM-based Backup Key Vault will make a key permanently inaccessible after a limited number of unsuccessful attempts to access it. WhatsApp has stated that it will simply be aware that a key exists, but will not be aware of the key itself.
In the Backup Key Vault, how will WhatsApp store encryption keys?
WhatsApp will handle client connections and client-server authentication through its front-end service, ChatD, and will create a protocol that delivers keys to and from its servers. During this time, encrypted messages will be exchanged between the user’s smartphone and the HSM-based Backup Key Vault. ChatD will not be able to access the messages sent between the client’s phone and its servers, according to the business.
According to the firm, the HSM-based Backup Key Vault service would be geographically distributed across different data centers to correctly handle encryption keys and ensure their availability at all times. This will aid in keeping the backup keys operational in the event of a data centre outage.
Backup Key Vault based on HSM, as well as the encryption and decryption procedure
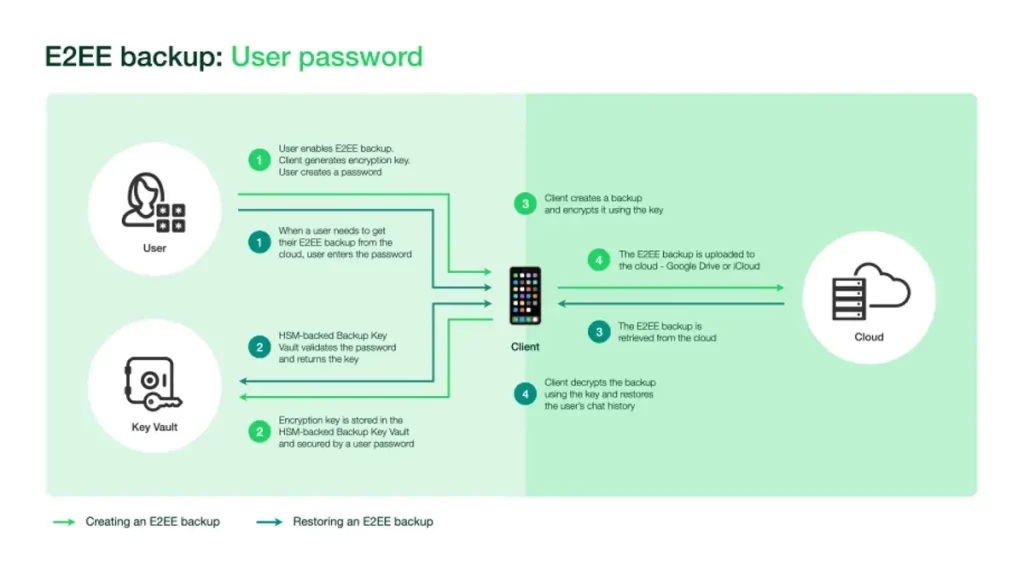
When a user selects to protect their end-to-end encrypted backup with a personal password, their key is delivered to the HSM-based Backup Key Vault for storage and protection.
To obtain a key, a user must follow the steps outlined below:
- Enter the password, which the Backup Key Vault will validate.
- The encryption key will then be returned to the user’s smartphone by the Backup Key Vault.
- The user can now decode their end-to-end encrypted backups using their smartphone.
Follow Crispbot on Facebook and Twitter. For the latest news, tech news, breaking news headlines, and live updates checkout crispbot.com














0 Comments